VARIANTE DE CRYPTXXX O ULTRACRYPTER PERO QUE NO AÑADE EXTENSION A LOS CIFRADOS Y QUE PASAMOS A IDENTIFICAR COMO TROJAN ENCODER
Nos ha llegado una nueva variante de ransomware parecida a los anteriores CRYPTXXX con diferencias pero con similitudes en su presentación:
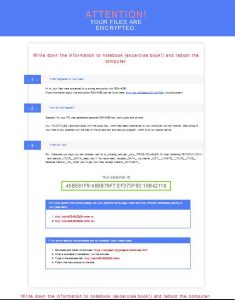
que en texto plano dice lo siguiente:
«What happened to your files ?
All of your files were protected by a strong encryption with RSA4096
More information about the encryption keys using RSA4096 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
How did this happen ?
!!! Specially for your PC was generated personal RSA4096 Key , both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
!!! Decrypting of your files is only possible with the help of the private key and decrypt program , which is on our Secret Server
What do I do ?
So , there are two ways you can choose: wait for a _miracle_ and get _your_ PRICE DOUBLED! Or start obtaining *BITCOIN NOW! , and restore _YOUR_ _DATA_ easy way
If You have really valuable _DATA_, you better _NOT_ _WASTE_ _YOUR_ _TIME_, because there is _NO_ other way to get your files, except make a _PAYMENT_
Your personal ID: 45B561F9:488B79F7:EF373F93:10B42110
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1 – http://ccjlwb22w6c22p2k.onion.to
2 – http://ccjlwb22w6c22p2k.onion.city
If for some reasons the addresses are not availablweropie, follow these steps:
1 – Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2 – Video instruction: https://www.youtube.com/watch?v=NQrUZdsw2hA
3 – After a successful installation, run the browser
4 – Type in the address bar: http://ccjlwb22w6c22p2k.onion
5 – Follow the instructions on the site «
___________________________
y el fichero infector está en una DLL: rad36384.tmp.dll
Entre las diferencias cabe indicar que no añade nada a la extensión de los ficheros cifrados
El preanalisis de virustotal ofrece el siguiente informe:
MD5 3ab7fd5bb3e34c4f14342514a3211828
SHA1 ddf9ff2f26e690956e908a95dc066fa64af2d0c7
File size 165.5 KB ( 169472 bytes )
SHA256: 43106209c2f00d3b9de898a3d08019460ff6f12c92bcf10422027c8c807240a1
File name: rad36384.tmp.dll
Detection ratio: 23 / 58
Analysis date: 2016-09-02 07:43:40 UTC ( 8 minutes ago )
0
1
Antivirus Result Update
AVG Win32/Cryptor 20160902
Ad-Aware Gen:Variant.Symmi.67903 20160902
AegisLab Virus.W32.Cryptor!c 20160902
AhnLab-V3 Trojan/Win32.CryptXXX.N2094585847 20160902
Arcabit Trojan.Symmi.D1093F 20160902
Avira (no cloud) TR/ATRAPS.phza 20160902
BitDefender Gen:Variant.Symmi.67903 20160902
Bkav W32.eHeur.Malware07 20160901
Cyren W32/Trojan.QGID-2562 20160902
DrWeb Trojan.Encoder.5879 20160902
ESET-NOD32 a variant of Win32/GenKryptik.CGL 20160902
Emsisoft Gen:Variant.Symmi.67903 (B) 20160902
F-Secure Gen:Variant.Symmi.67903 20160902
Fortinet W32/GenKryptik.CGL!tr 20160902
GData Gen:Variant.Symmi.67903 20160902
Invincea virus.win32.ramnit.ah 20160830
Kaspersky Trojan-Ransom.Win32.CryptXXX.xcw 20160902
McAfee Artemis!3AB7FD5BB3E3 20160902
McAfee-GW-Edition Artemis 20160902
eScan Gen:Variant.Symmi.67903 20160902
Microsoft Ransom:Win32/Tovicrypt.A 20160902
Panda Generic Suspicious 20160901
Rising Malware.Generic!IegnW1psKzK@1 (thunder) 20160902
Lo pasamos a controlar a partir del ELISTARA 35.12, ya disponible en nuestra web
saludos
ms,. 2-9-2016
NOTA: Los interesados en información sobre contrato de soporte Asistencia Tecnica de SATINFO y/o licencia de uso/actualizaciones de sus utilidades, contacten con info@satinfo.es
__________
Este blog no se hace responsable de las opiniones y comentarios de los textos en los que se cita la Fuente, ofreciendo su contenido solo para facilitar el acceso a la información del mismo.
You can follow any responses to this entry through the RSS 2.0 feed. Both comments and pings are currently closed.

Los comentarios están cerrados.